- 03 Mar 2023
- 3 Minutes to read
- Print
- DarkLight
False Positive Rules
- Updated on 03 Mar 2023
- 3 Minutes to read
- Print
- DarkLight
To reduce the number of false positives, you may want to create False Positive (FP) rules. FP rules filter out detections generated by the report action of Detection & Response rules. These rules apply globally across all rule namespaces and targets.
There are multiple ways to create a False Positive rule in LimaCharlie web app.
Similarly to Detection & Response rules, False Positive rules are created on a per tenant level. This means that if you have more than one organization you want to apply the rule to, you will want to
- re-create the same rule in multiple organizations, or
- using our infrastructure as code functionality, push your FP rules to multiple tenants within seconds.
Use Cases
The typical use case for FP rules is to add exceptions from some detections that are cross-cutting (for example ignore all detections from a specific host), organization-specific exceptions (like ignoring alerts relating to a custom piece of software used in an organization), or suppressing errors from managed D&R rules you don't have direct access to.
Structure
False positive rules are structured roughly the same as the Detection part of a D&R rule. The main difference is that instead of a direct event, the rule applies to the content of a detection, as can be seen in the Detections section of the web app.
The originating event for the detection can still be accessed at the detect path. This means that if ignoring something based on the event content, we only need to add detect/ to the front of the path (see example).
Create a False Positive rule from detections
This is the quickest and the most common way to create a FP rule. On every detection, you can click the Mark False Positive button.
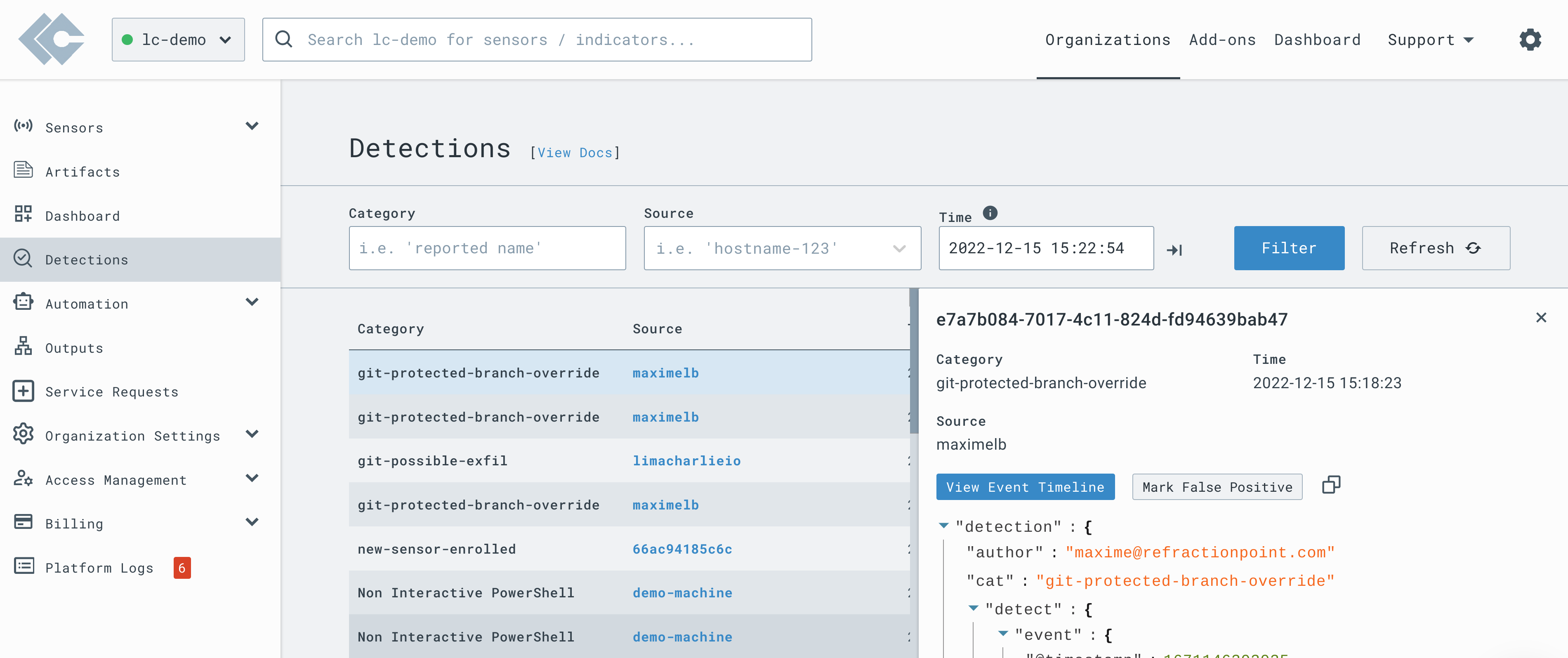
Clicking the button will pre-populate the details of the event and automatically generate a draft False Positive rule which you can edit before saving.
After the rule is saved, it will appear in the False Positives Rules section and can be edited/deleted there.
Create a False Positive rule from scratch
While creating FP rule from detections is a common and easy way to reduce the number of false positives, you do not need to wait for the detection to happen before creating a FP rule. The FP Rules section under Automation allows you to create a False Positive rule from scratch.
To create a new False Positive rule, click the New Rule button.
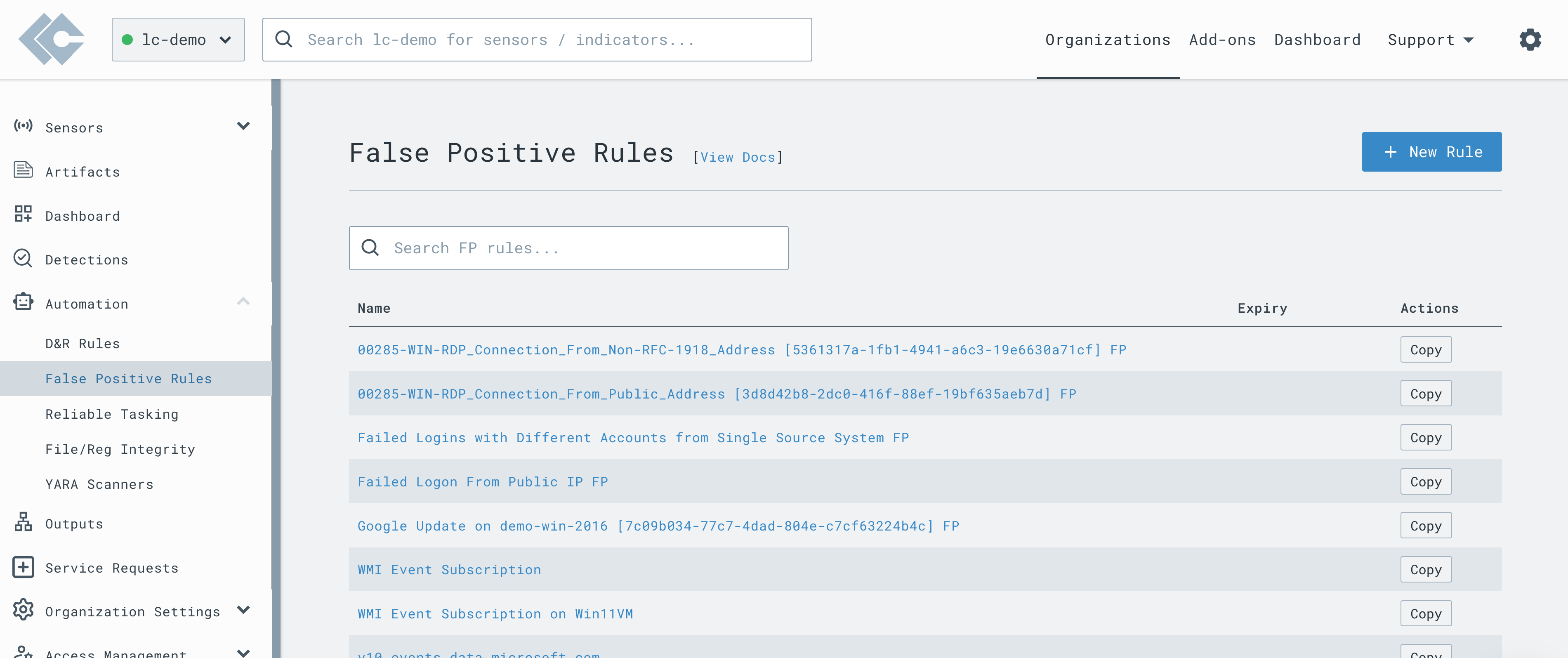
This will open a rule editor allowing you to create a new rule.
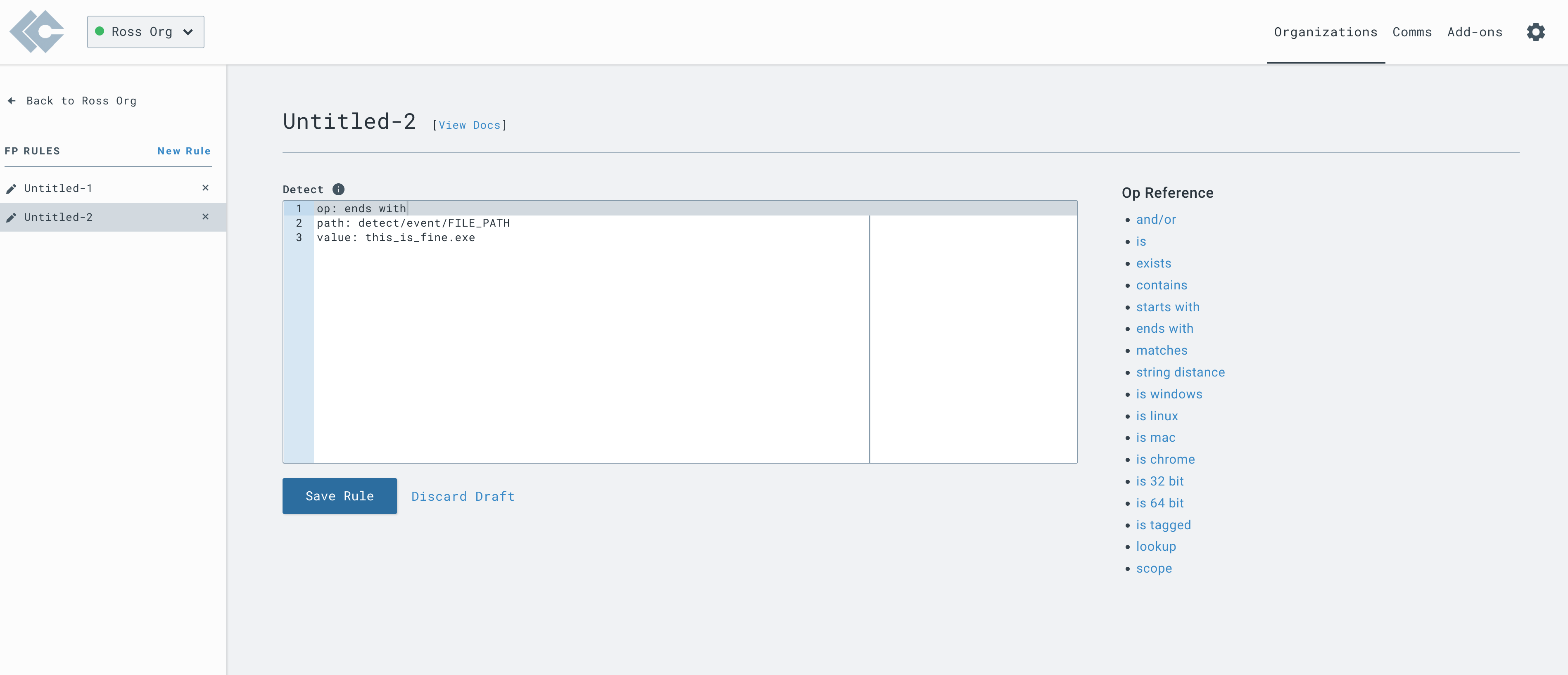
An FP rule is structured with the same format at the detection component of a D&R rule. The main difference is that the rule applies to the content of a detection, as can be seen in the Detections section of the web app.
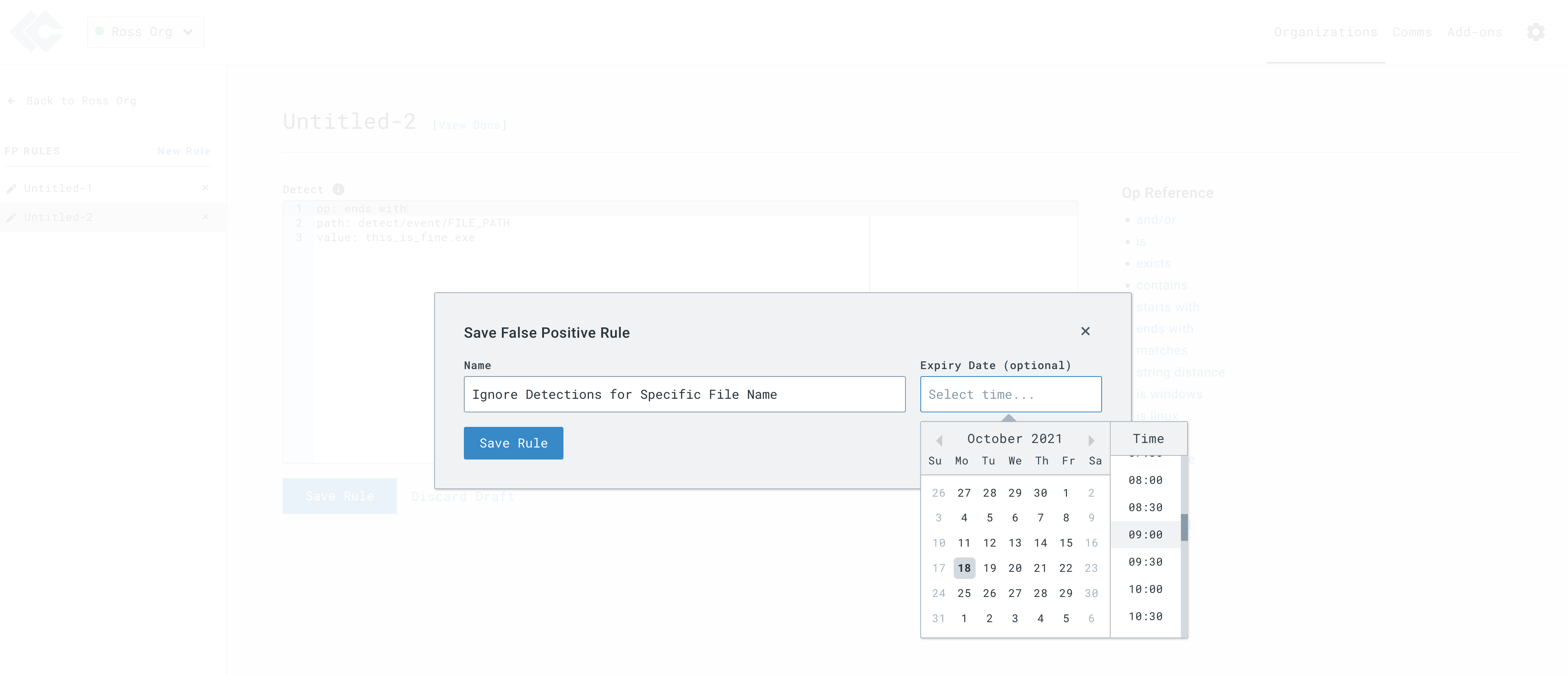
After you click Save Rule, you will get the ability to set a rule name as well as an Expiry Date (optional). Setting an expiry date allows you to create a rule that will expire at a certain time.
Please note that expiry times must be set in the user's preferred time (not in UTC).
Examples
Clicking the button will pre-populate the details of the event and automatically generate a draft False Positive rule which you can edit before saving. The details about the structure of the False Positive rules can be found in our technical documentation.
Suppress a Specific Detection
Prevent a specific detection:
op: is
path: cat
value: my-detect-name
Ignore Detections for Specific File Name
Ignore any detection that relates to a file name in any path.
op: ends with
path: detect/event/FILE_PATH
value: this_is_fine.exe
Ignore Detections on a Specific Host
Any detection originating from a specific host will be ignored.
op: is
path: routing/hostname
value: web-server-2

