Transforming Output Data
- 23 Jan 2024
- 1 Minute to read
- Print
- DarkLight
This documentation version is deprecated, please click here for the latest version.
Transforming Output Data
- Updated on 23 Jan 2024
- 1 Minute to read
- Print
- DarkLight
Article summary
Did you find this summary helpful?
Thank you for your feedback!
When passing events to an output, you have the option to transform the original event in multiple ways. When creating an output, Custom Transforms are applied in the highlighted area of the screenshot below.
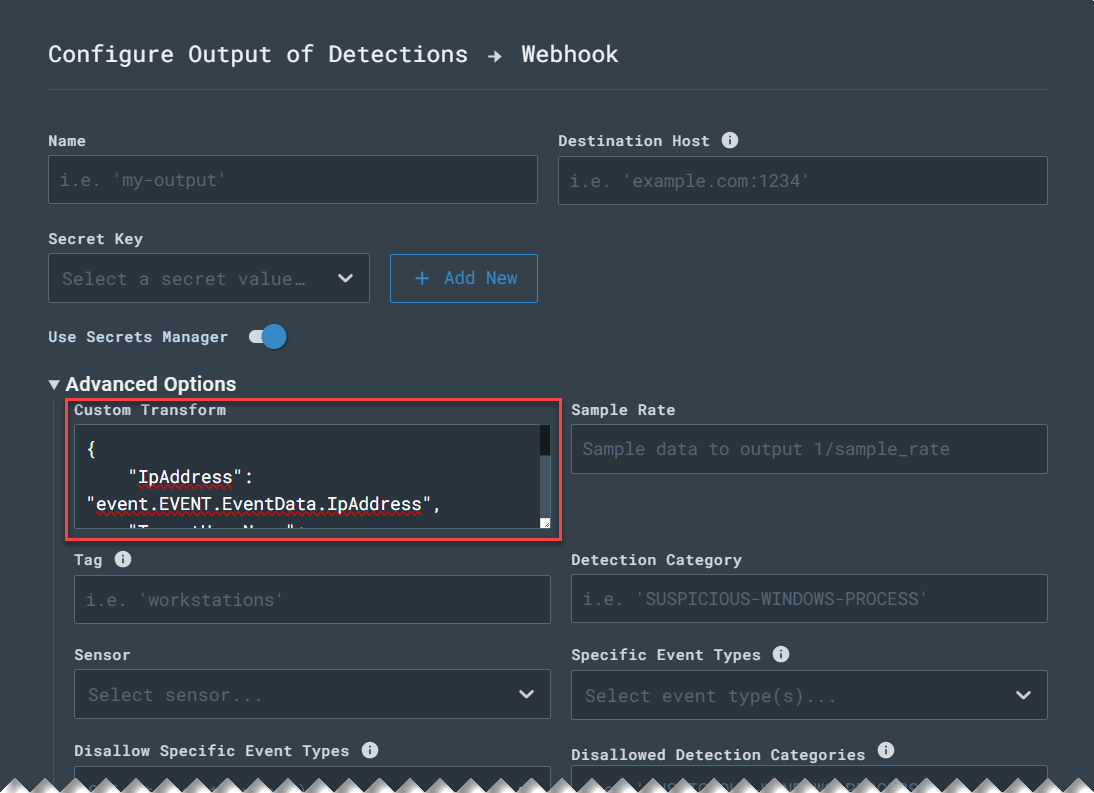
Examples
Extracting Fields from Telemetry
Let's say you have the following 4625 failed logon and you want to send similar events to an output, but only certain fields.
{
"event": {
"EVENT": {
"EventData": {
"AuthenticationPackageName": "NTLM",
"FailureReason": "%%2313",
"IpAddress": "142.99.21.14",
# <extra fields removed>
"TargetUserName": "administrator",
"WorkstationName": "D-483"
},
"System": {
"Channel": "Security",
"Computer": "demo-win-2016",
# <extra fields removed>
"EventID": "4625",
"EventRecordID": "22690646",
# <extra fields removed>
"TimeCreated": {
"SystemTime": "2024-01-23T17:30:07.345840000Z"
},
"Version": "0",
"_event_id": "4625"
}
}
},
"routing": {
# <extra fields removed>
"event_type": "WEL",
"hostname": "win-2016.corp.internal",
# <extra fields removed>
"tags": [
"windows"
],
"this": "8873fb9fcb26e2c0d4299ce765aff77d"
},
"ts": "2024-01-23 17:29:33"
}
The following Output Transform would extract only the IpAddress, TargetUserName, EventID, and SystemTime the event was created. Notice, the newly mapped field names can be whatever you want.
{
"Source IP": "event.EVENT.EventData.IpAddress",
"Username": "event.EVENT.EventData.TargetUserName",
"Event ID": "event.EVENT.System.EventID",
"Happened at": "event.EVENT.System.TimeCreated.SystemTime"
}
The following example outputs text and specified fields using Template Strings.
{
"text": "Failed logon by {{ .event.EVENT.EventData.TargetUserName }} on {{ .routing.hostname }}"
}
The above example would generate the following output using the provided sample WEL.
{
"text": "Failed logon by administrator on win-2016.corp.internal"
}
Was this article helpful?

