- 27 Jul 2023
- 2 Minutes to read
- Print
- DarkLight
Ingesting Linux Audit Logs
- Updated on 27 Jul 2023
- 2 Minutes to read
- Print
- DarkLight
One data source of common interest on Linux systems is the audit.log file. By default, this file stores entries from the Audit system, which contains information about logins, privilege escalations, and other account-related events. You can find more information about Audit Log files here.
There are a few techniques to ingest Linux Audit logs into LimaCharlie:
- Pull the raw logs using Artifacts and/or the File System navigator (EDR sensors only)
- Collect the files using Artifact Collection.
- Stream the raw audit log via a
fileadapter.
We will explore these techniques in this tutorial. Adapters can also be configured as syslog listeners; that will be covered in another tutorial.
File System Browser
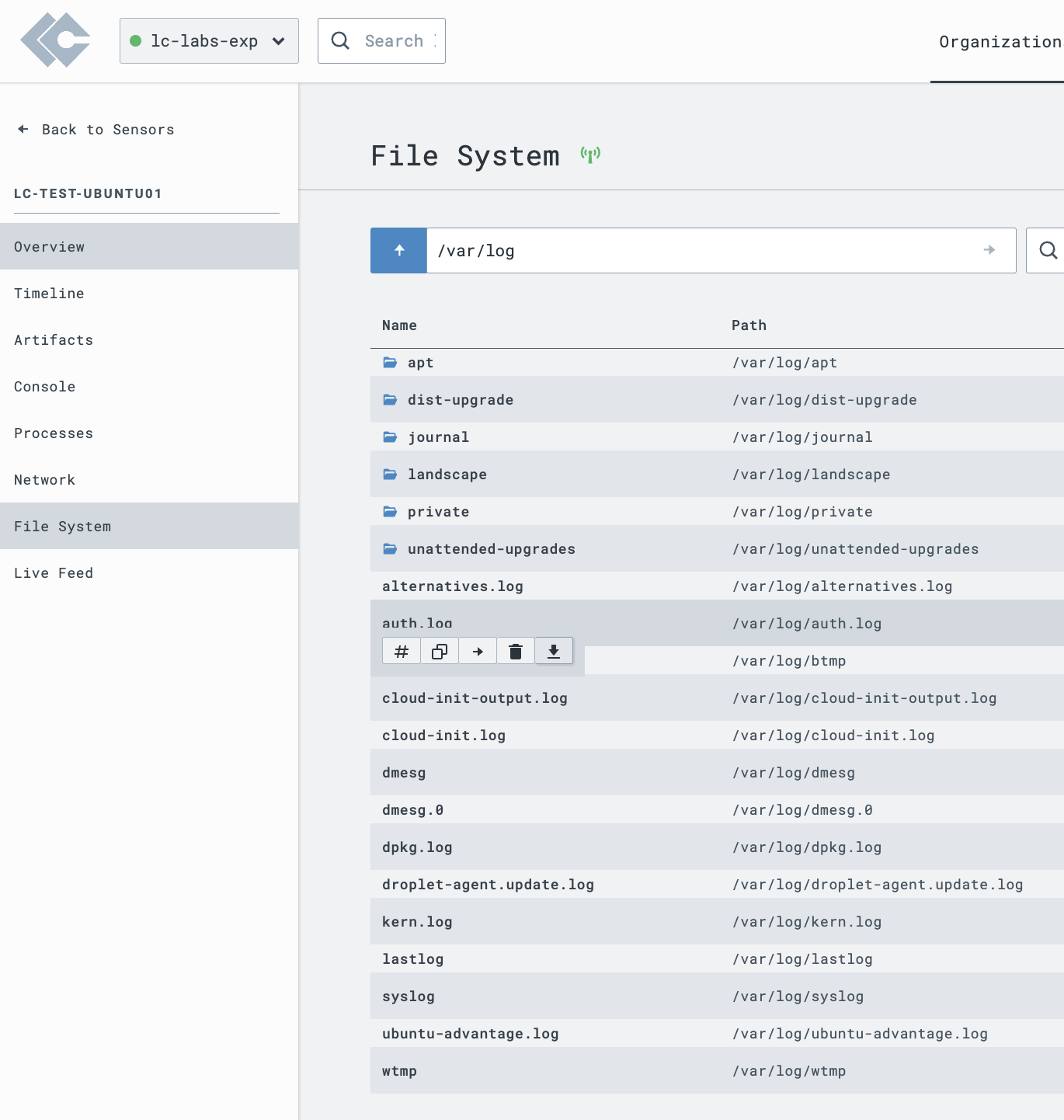
Our Windows, Linux, and macOS EDR sensors offer file system navigation capabilities. If you need a single, ad-hoc collection of the auth.log, you can use the File System capability to navigate to /var/log, and download auth.log.
Artifact Collection
If you don't need to stream Linux audit log(s), but instead want to maintain a copy of them for posterity, Artifact collection would be your best method. This is an automated collection technique, but won't stream the events to your Timeline.
Step 1: Within the Navigation Pane, select Artifact Collection.
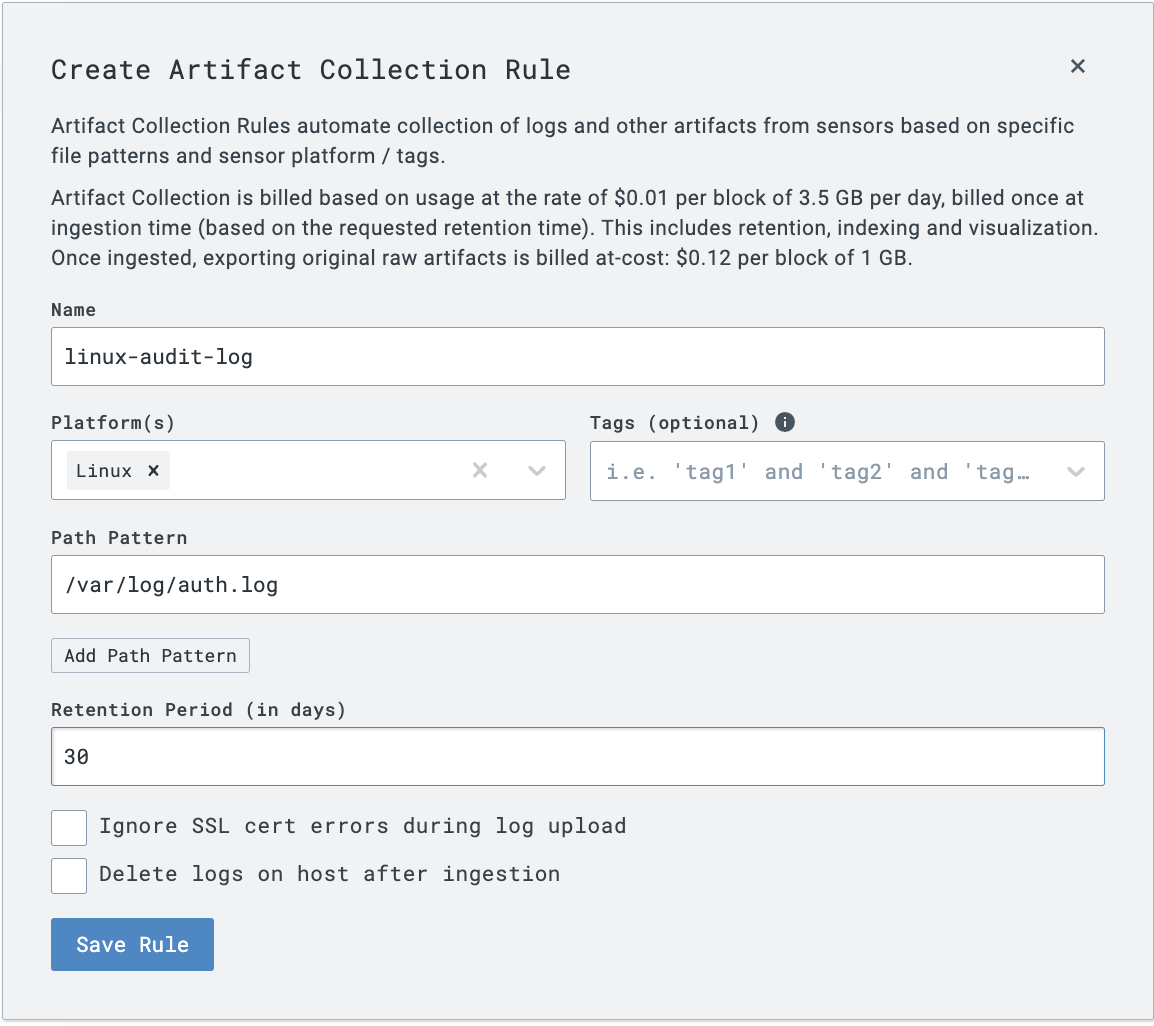
Step 2: Create a simple Artifact Collection Rule for /var/log/auth.log. In this example, we chose a retention period of 30 days; however, you should choose the correct retention period for your use case.
Step 3: Saving the Artifact Rule will then populate to the appropriate sensor(s), and you should see the auth.log in the Artifacts menu, once it is collected by the Sensor.
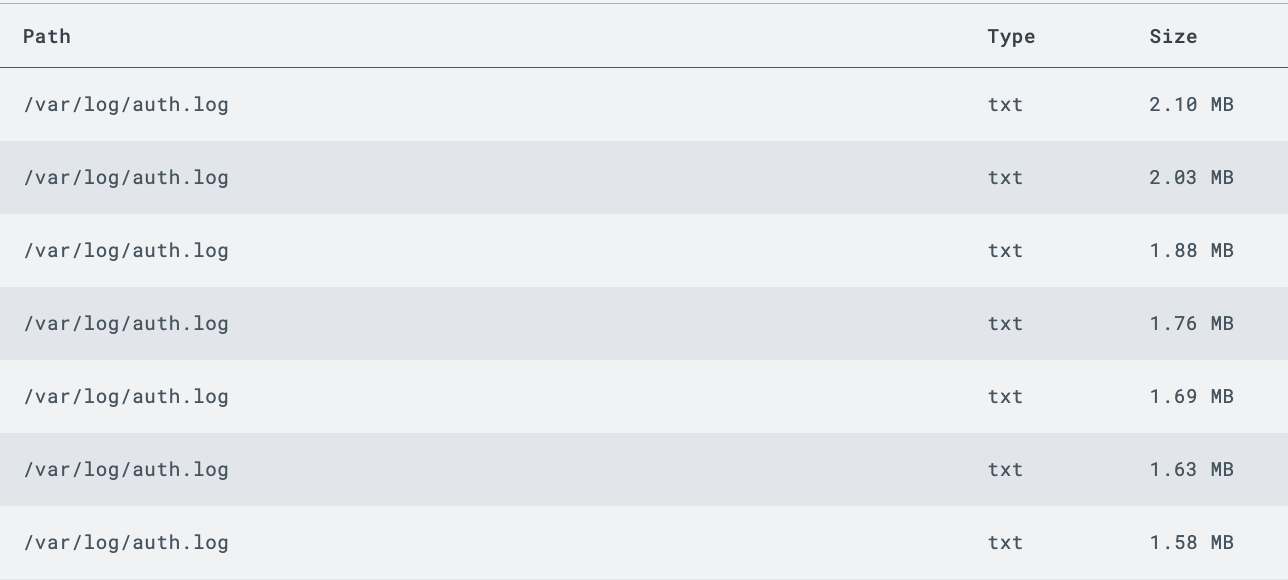
Want more than just the most recent auth.log? Specify a regular expression to capture all archived copies of the log files. However, be careful on retention and make sure you're not unnecessarily duplicating data!
File Adapter Ingestion
It is also possible to deploy a LimaCharlie Adapter pointed to auth.log to collect and stream the events in directly. Note that Adapters will create a separate telemetry "stream" - thus, it is recommended to combine file types where possible.
Step 1: Create an Installation Key for your adapter and download the appropriate binary.
Step 2: On the system(s) to collect logs from, deploy the adapter. We recommend utilizing a configuration file for adapter testing, to allow for tracking of changes. The following is a sample file that will ingest auth.log events as basic text.
file:
client_options:
identity:
installation_key: <installation_key>
oid: <oid>
platform: text
sensor_seed_key: audit-log-events
file_path: /var/log/auth.log
no_follow: false
More details on configuration files and Adapter usage can be found here.
Step 3: Run the adapter, providing the file option and the appropriate config file.
$ ./lc_adapter file /tmp/config.yml
The Adapter should load the config and display options to the terminal.
Note: This is not a persistent install; utilize your operating system's init/systemctl capabilities to create a persistent adapter
Step 4: Returning to the LimaCharlie web UI, you should start to see events flowing in almost instantaneously.
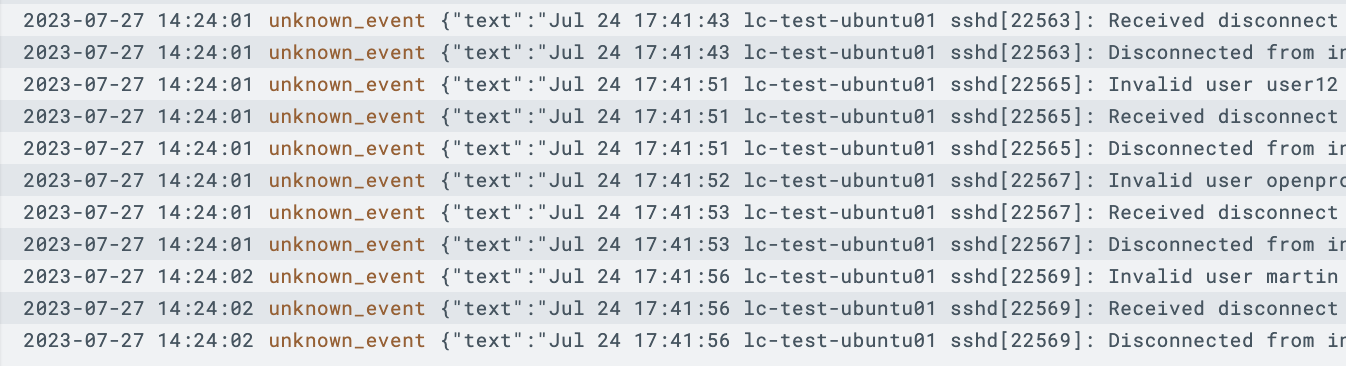
Note that a text platform will ingest data as basic text, however you could use formatting options to parse the fields respective to your auth.log format.

