- Print
- DarkLight
Microsoft Entra ID, formerly Azure Active Directory, is an identity and access management solution from Microsoft that helps organizations secure and manage identities for hybrid and multicloud environments.
The Entra ID API Adapter currently receives risk detection alerts, as generated by Entra ID’s Identity Protection feature. You can learn more about these detections here: https://learn.microsoft.com/en-us/entra/id-protection/concept-identity-protection-risks. Data received via an Azure Event Hub or Webhook will be unique to your custom output parameters.
Entra ID events are recognized as the azure_ad platform.
Adapter Deployment
Microsoft Entra ID logs are ingested into LimaCharlie via:
Azure Event Hub
Entra ID API
Webhooks
Azure Event Hub
Within the LimaCharlie web app, there is a helper that can be used to easily configure receiving Entra ID events via an Azure Event Hub.
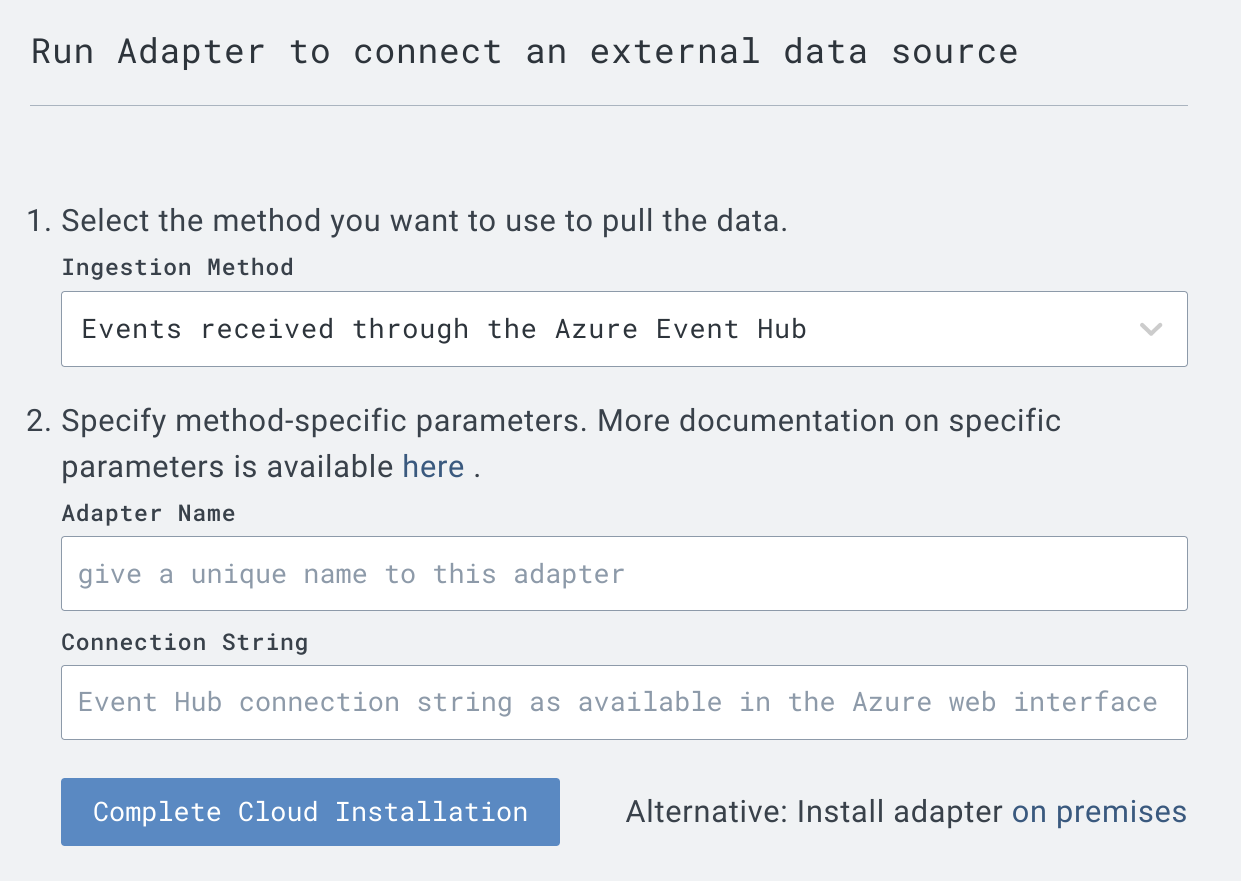
If utilizing the helper, only two fields are needed:
Name for the adapter
Connection string to the Azure Event Hub
You can find more information about Azure Event Hub Adapters here.
Documentation for creating an event hub can be found here here.
Entra ID API
To collect data via the Entra ID API, you’ll need to configure an App Registration in Azure and ensure it has the correct permissions.
In Azure, navigate to the Entra ID Overview page. Select App Registrations and click
+ New Registration.Name the application, and select the Supported account types.
After registering an App, you’ll be provided metadata for that application. Take note of the
Application (client) IDandDirectory (tenant) IDfields, as you will need them for configuration.Select Add a certificate or secret, and create a new client secret. Provide a description and select an applicable Expiration time. Note: You will need to refresh the Secret in LimaCharlie once it expires!
After creating the secret, copy the
Secret Value. You will need this to configure the LimaCharlie Adapter.Navigate to the Manage > API permissions menu for your newly-created application. Ensure that the following permissions have been enabled:
IdentityRiskEvent.Read.All
IdentityRiskEvent.ReadWrite.All
IdentityRiskyServicePrincipal.Read
IdentityRiskyServicePrincipal.ReadWrite.All
IdentityRiskyUser.Read.All
IdentityRiskyUser.Read.Write.All
User.Read (default)
Create a new Adapter within LimaCharlie, and select Microsoft Entra ID. Select Microsoft Entra ID API as the ingestion method. You should see a dialog box like the following:.png)
Name the Adapter and provide the following details:
Tenant ID
Client ID
Client Secret
Note: You can use the Secrets Manager for these values if you wish!
Click Complete Cloud Installation, and the Adapter should be created successfully. Monitor the Platform Logs for any errors.
Note: As previously mentioned, the API Adapter receives events from the Risk Detections API. You will only receive events when these events are sent by the platform. Thus, if you’re not receiving any events immediately after Adapter creation, this may be due to no risky events occurring!
Webhooks
Within the LimaCharlie web app, there is a helper that can be used to easily configure receiving Entra ID events.
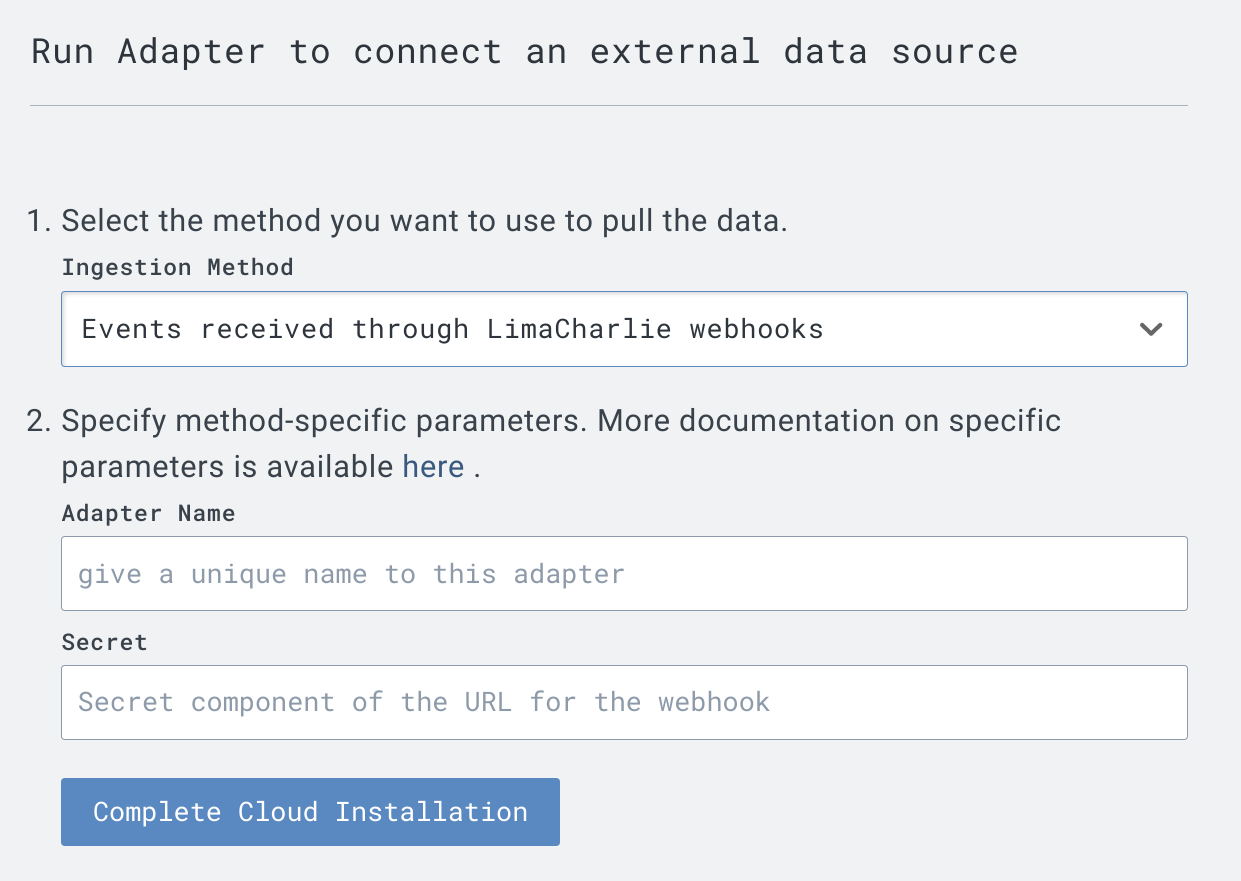
If utilizing the helper, only two fields are needed:
Name for the adapter
Secret component of the URL for the webhook
More information about creating a webhook and obtaining the completed URL, utilizing the secret component, can be found here.



